Programas con titulaciones oficiales en Panamá, Colombia, Ecuador y México y convenios con UMECIT, IPIA y Fundación Universitaria Los Libertadores.
Intensive programmes
Extracurriary programs focused on bringing the world closer to the youngest of technology: programming, artificial intelligence, electronics, video games, cybersecurity, etc...
The best defence is a good attack, or at least that is how it is in cybersecurity. From this concept comes the concept of pentesting, which allows weaknesses in a device, in this case a virtual machine, to be revealed and corrected.
Pentesting, or ethical hacking, simulates all kinds of attacks in order to find the weak points of a system that would not withstand a real attack, dedicating efforts to strengthen them and ensure that they will not be repeated.
Carried out by Andrés Orozco Noreña | Ernesto López Bravo | Luis Miguel Rodríguez
Qualification Cybersecurity Master
Technologies DoubleTrouble | Kali Linux | Metasploit | NMAP | ARP | GoBuster | StegSeek | Steghide | Searchsploit | Hacker Kid | Hacker Kid | Searchsploit | Searchsploit | Searchsploit | Searchsploit | Hacker Kid
⭐Best Capstone Award 2024
Cybersecurity is key in an increasingly technological world and, at the moment, there is no more reliable way to understand how a cybercriminal works than by mimicking it. An ethical hacking process simulates a real attack, finding weaknesses and vulnerabilities, so that they can be addressed. In recent years, numerous techniques and procedures have emerged that allow these tests to be carried out more efficiently and to counter the advances of cybercrime.
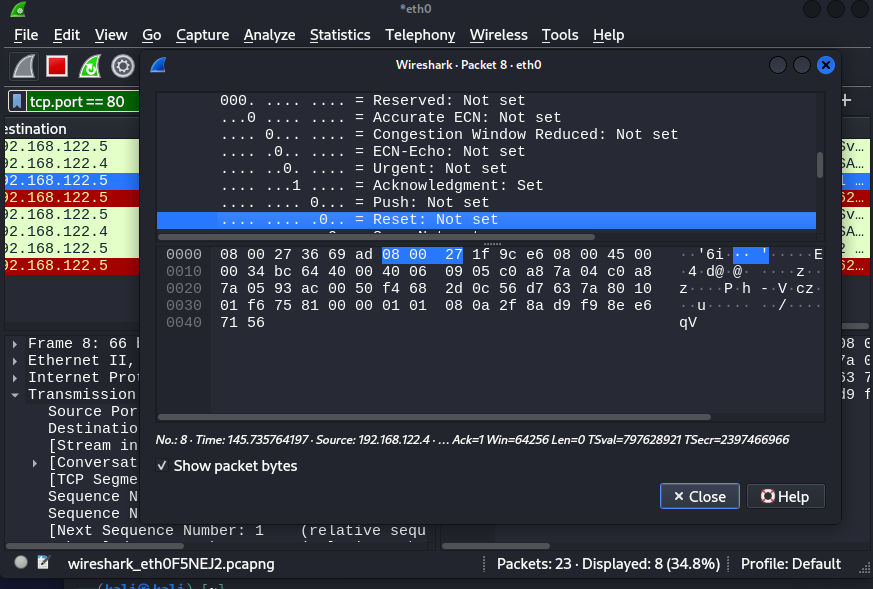
The ethical hacking process followed several steps, which employed a variety of pentesting techniques:
This ethical hacking process revealed numerous vulnerabilities in the virtual machine, such as compromised ports and injected code, through non-intrusive scanning so that traffic was not blocked and raised no alarms. All vulnerabilities found were compiled in a report in order to have a complete overview and facilitate the resolution of all issues, thus preventing different types of attacks and problems.
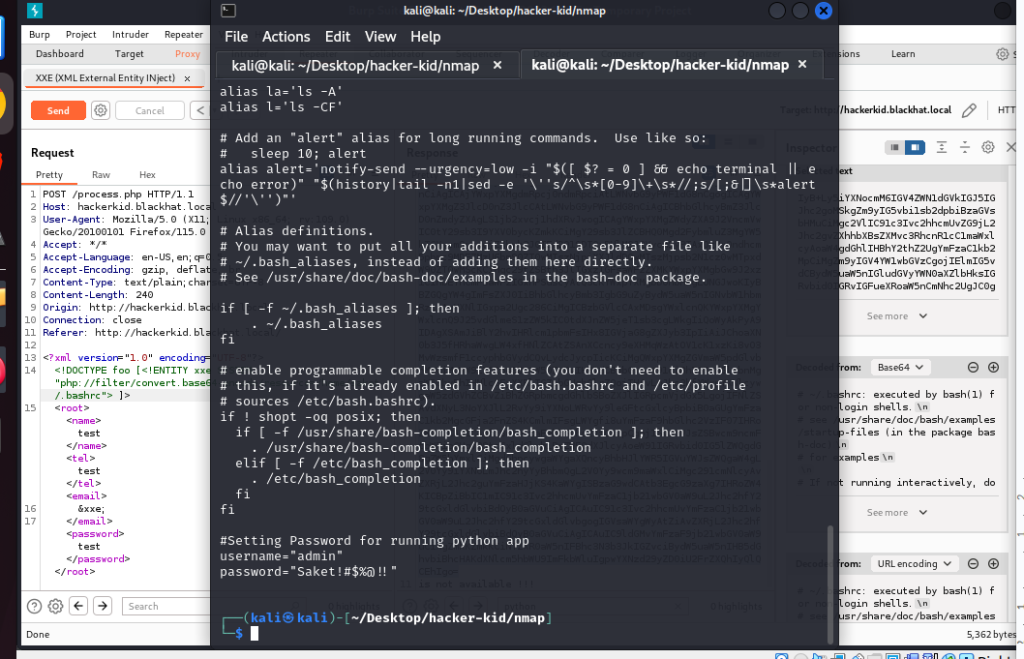
Ethical hacking has become an essential process for any organisation, as it is a proactive way to stay ahead of cybercriminals and keep all assets safe. It also provides security recommendations, both for devices and the people who interact with them.