Programas con titulaciones oficiales en Panamá, Colombia, Ecuador y México y convenios con UMECIT, IPIA y Fundación Universitaria Los Libertadores.
Intensive programmes
Extracurriary programs focused on bringing the world closer to the youngest of technology: programming, artificial intelligence, electronics, video games, cybersecurity, etc...
Cloud adoption means that the right cyber security configurations need to be in place in order to avoid vulnerabilities. To do this, you need to be able to identify them correctly.
The AWS Goat service enables simulations of attacks within the AWS environment to assess the security of the cloud infrastructure. This service makes it easier to understand common vulnerabilities in the cloud, so that the cybersecurity team can protect the organisation's critical data and services.
Carried out by Sofia Martinez | Marco Funes | Alam Pérez Aguiar | Emilio Ocejo
Qualification Cybersecurity Master
Technologies AWS Goat | GitHub | GitHub | Terraform Apply | NMAP | BurpSuite | AWS CLI | OWASP ZAP | SSH
Migrating from on-premise servers to the cloud means that security no longer only applies to the hardware and devices you have in your organisation, but extends to your chosen cloud environment. The provider is responsible for part of that security, but customers also have their share of the responsibility. In order to understand the weaknesses of this type of environment, services such as AWS Goat are used to simulate attacks and carry out a pentesting process to identify vulnerabilities and study possible solutions.
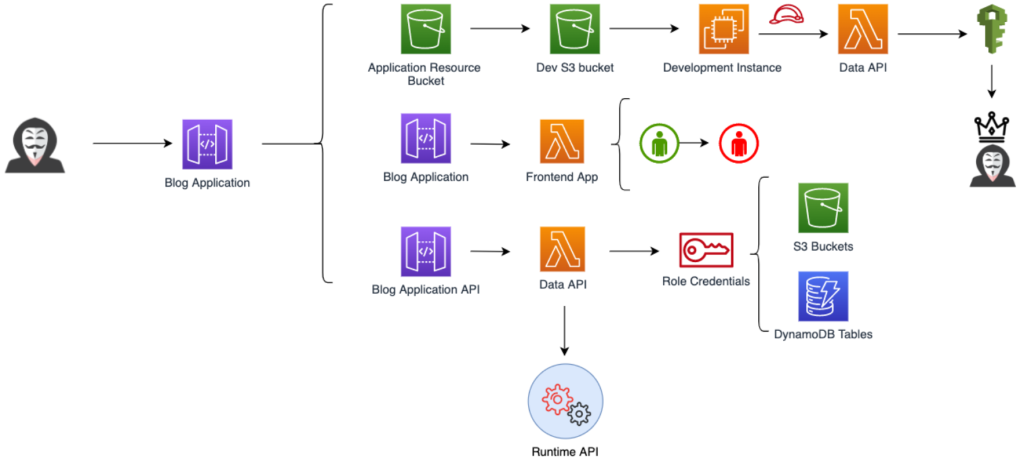
The cloud brings a new element that must be correctly configured in terms of cybersecurity. In order to understand this new environment in the most appropriate way possible, the following has been done:
Studying the vulnerabilities allowed various types of tests to be carried out to test the criticality of these weaknesses:
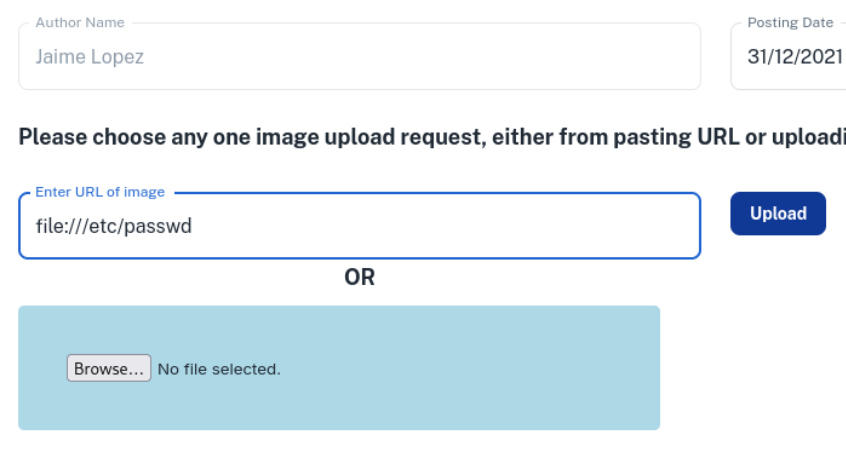
The audit revealed multiple critical vulnerabilities, especially in elements related to access controls, exposure of sensitive data and code injections. These required urgent mitigation by strengthening access policies and credential management. Strict recommendations and controls were also implemented, culminating in constant review and monitoring to ensure the continued protection of cloud resources.